Distributed Denial of Service (DDoS) attacks threaten any online business. This blog submit is about how to combat this website-destroying chance with one of the handiest solutions feasible – a DDoS Protected VPS.
In this put-up, you’ll study the capacity dangers of a DDoS with useful figures from the effects of new DDoS assaults. You may also study the many myths and statistics on this vicinity. To finish, we will talk about an effective approach to safeguarding your server in opposition to destiny DDoS assaults.
One thing is genuinely authentic: A DDoS can convey your business to a halt and motivate it to go offline in mere mins. Simply placed, any tourist will no longer be capable of getting admission to your website. This is because those attacks weigh down a server’s assets and/or bandwidth to stop users from getting access to their preferred online packages.
It is a superb concept to also be aware of the actual risk of struggling with a DDoS attack, before investing any of your money on an Anti-DDoS answer. Let’s start reading the level and types of threat that you are in all likelihood to stand.
What is the real risk of a DDoS Attack?
While causing your internet site to be inaccessible can also appear handiest and inconvenient, it’s far commonplace for DDoS attacks to be used for ways greater dangerous cybercrime sports. These can consist of sports along with Virus infections, Malware activations, Network Breaches, Data Breaches, Financial Theft, and so on.
1 Loss of Revenue.
Your online enterprise is in all likelihood a chief supply of sales. Consider the quantity of revenue you could lose in case you came under attack from a DDoS. Imagine if your critical net programs or offerings stopped responding.
During the peak income time, the hourly revenue loss caused by a DDoS assault relies upon the kind and length of the company. Astoundingly, nearly 66% reported a lack of sales that came in between $25k to $250k.
2 Data Breach
DDoS attacks frequently offer camouflage for greater unfavorable and beneficial crimes. This can imply, as an instance, locating unlawful access points on your network and stealing touchy statistics.
To address this, security staff have to be vigilant. This is not best to reduce the results of the DDoS itself however also to keep the focus on any feasible subsequent intrusion.
They have to additionally make more than one backup of task-critical information, preferably allotted redundantly throughout multiple locations. These must be secured in opposition to capability exposure or deletion.
3 Loss of Customer Confidence
Network and Web carrier availability is critical for preserving purchaser trust. It is also crucial for their pride, which leads directly to the ease of acquiring new customers.
We hardly ever want to say that that is extremely important in one of this aggressive marketplace. In a DDoS attack, essential infrastructure is commonly focused. Unsurprisingly, this may impact community performance.
This leads immediately to unhappy clients. Perhaps they’ll circulate some other place, or perhaps word of mouth will unfold regarding this dissatisfaction, making it extra hard to draw valuable new customers.
This offers a chief difficulty for service-offering industries, including Web Hosting vendors, which depend closely on consumer believe to keep their business.
4 Degradation of Reputation
Brand popularity is a key factor in commercial enterprise success. When an enterprise is incapable of supplying its services, clients lose their self-belief in your emblem. In turn, this can degrade your popularity inside the enterprise. An applicable and well-known piece of commercial enterprise information involves the mind:
Once a commercial enterprise’s reputation has degraded or been lost, it turns into uphill warfare for a business enterprise to get better. Getting new customers to believe them ever once more becomes a herculean assignment.
5 Ransom
In the latest months, cyber attackers have come to be extra inquisitive about ransom. This is with the aid of threatening corporations with a DDoS attack towards their maximum vital, task-vital online systems.
Normally, cybercriminals will surely ship out a message threatening to perform an RDDoS (Ransom driven DDoS assault), except the asked ransom is paid by way of a given closing date.
Occasionally, cybercriminals may additionally launch a small DDoS assault. This is true to show that they are both critical and capable. They will then in all likelihood continue to maintain organization offerings ransom as in line with the above till a ransom is paid.
6 Incremental Help Desk Expenses
When your services forestall responding, your clients will flood you with calls and provider desk emails. To deal with the expanded quantity, additional Help Desk charges could be incurred. This is because it will be important for the company to have every person at their desk, lest it dangers drowning below consumer proceedings.
Experience additionally indicates that Hosting vendors have a better hazard of suffering a DDoS attack as compared to maximum other online organizations. This is due to the fact an assault on one client can mixture the risk onto all customers, because of the Hosting provider’s reliance on shared infrastructure for its patron’s websites.
What attract hackers to undertake DDoS attacks?
Mostly, attackers will demand which you pay them a hefty amount of money to keep away from any provider disruption in the first region.
For an individual or an enterprise, it is tough to identify the exact cause at the back of DDoS assaults.
This is because of the secret assets which might be controlling the computer systems that ship false traffic requests to the targeted system.
Now, you ought to now be thinking “What certainly motivates hackers to undertake DDoS attacks?”.Well, there’s a numerous set of motives. Let’s visualize some with the subsequent infographics, detailing the most commonplace nasty motivations.
What is a DDoS Protected VPS?
A Distributed Denial-of-Service (DDoS) protected VPS is a VPS with DDoS mitigation covered. This is also named an ‘Anti-DDOS VPS’, indicating that it’s far located on a server or server farm this is hardened in opposition to DDoS attacks.
This calls for an excessive records transmission restriction. It also requires strong hardware firewalls that can halt a DDoS attack in its steps, before it is able to get up to any mischief.
A DDoS Protected VPS should be capable of resisting the common types of DDOS attacks listed below.
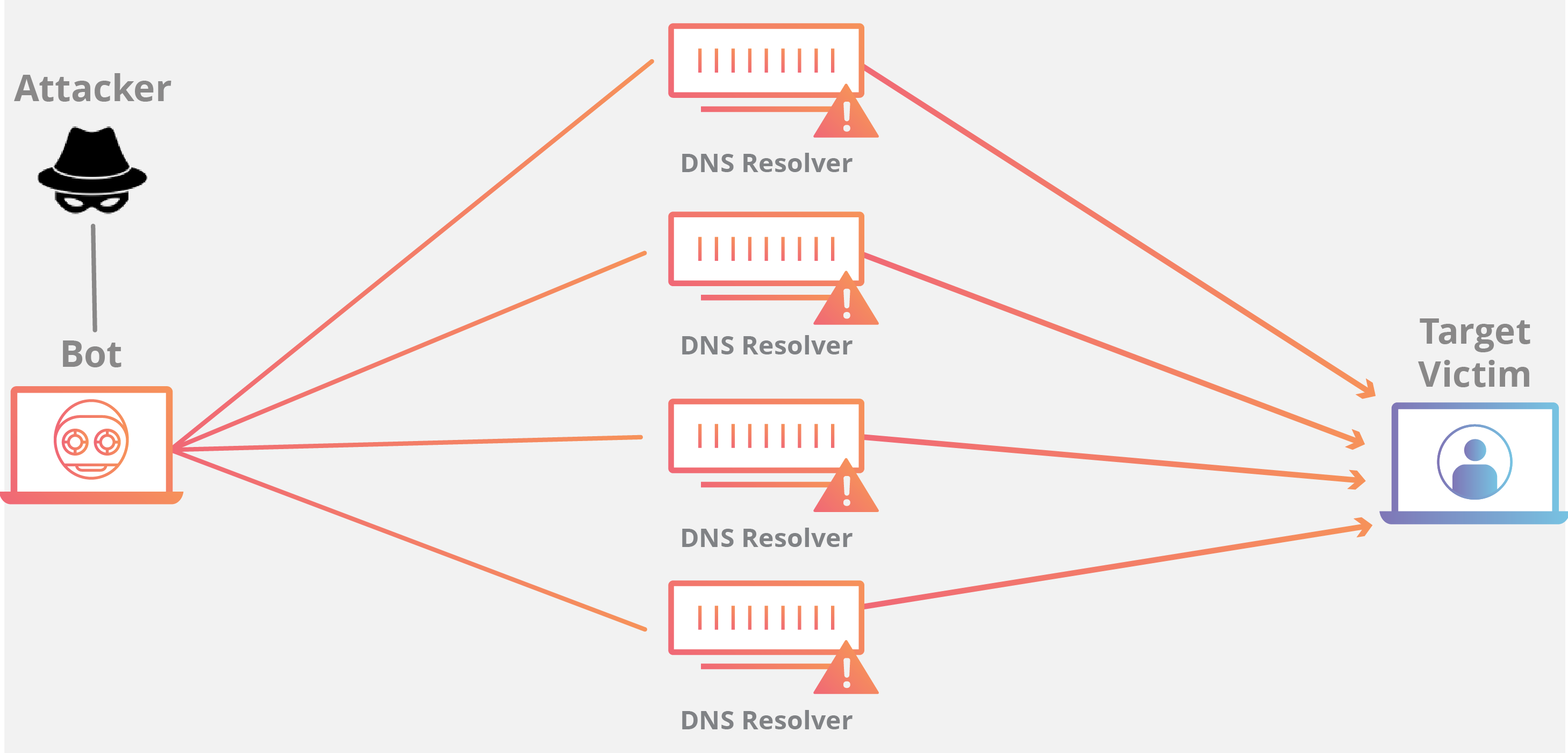
DDoS volumetric attacks (a faux site visitors flood.)
Protocol-primarily based assaults (malicious traffic which affects the manner facts are transferred.) Attacks on a specific server or user applications (e.G. WordPress.)
Most cheap web hosting vendors do now not encompass protection towards DDoS assaults. This is as it ends at better jogging prices.
KLCWEB includes DDoS safety. This is going up to 5Gbps regardless of their simple offerings. If you want greater, better volume protection is straightforward to shop for.
You must also ask your company how an awful lot of smooth facts can skip via and the quantity to which an assault can be resisted for the duration of a DDoS attack.
It is also critical to know the answer to the subsequent query!
Which types of DDoS Attacks can be stopped with a DDoS Protected VPS?
To cast off DDoS attacks, a DDoS Protected VPS is the most dependable solution. In short, it’ll forestall DDoS attacks and prevent attackers from disrupting your systems.
Let’s glance through the maximum famous types of attacks that can be halted with a DDoS Protected VPS.
1. ICMP (Ping) Flood
ICMP (Ping) flooding is one of the most popular Denials of Service assaults. With this assault, the attacker takes the sufferer’s device down through overwhelming it with ICMP echo requests.
The attackers send packets as quick as viable, not even waiting for the server to reply. The sufferer’s server will respond with an ‘Echo’ response. These will finally reason the gadget to go non-responsive or gradual down.
2. UDP Flood
UDP flooding is an alternative method of DDoS attack in which the attacker overwhelms random ports on the target server. The main goal of such an attack is simply to flood random ports on a given remote server.
The victim’s server checks for the application associated with the port and sends the answering packet. Of course, given the volume of requests, the system will ultimately become inaccessible to other clients.
3. Ping of Death
The Ping of Death is a particularly scary kind of Denial of Service assault wherein the attackers try to crash, destabilize, or freeze the centered server through sending malformed or outsized packets, the use of a ping command.
This can motive the memory buffers allocated to the packet to overflow, causing a denial of the provider for the legitimate packet. Generally, PoD assaults take advantage of legacy weaknesses present in an unpatched or prone system.
4. HTTP Flood
With HTTP flooding, the attackers control HTTP and POST requests to assault a web server or an software. Such assaults normally take advantage of interconnected structures that have been maliciously taken over with malware, inclusive of Trojan Horses.
This assault is only whilst it forces the server or utility to allocate the most possible amount of sources in response to every unmarried request.
5. SYN Flood
An SYN flood exploits a well-known weakness in the TCP connection series. It is a completely unique shape of a DDoS assault wherein the attackers send a succession of SYN requests to the target device, to be able to devour server resources in the method.
This will in the end render the device inaccessible for legitimate traffic. In this DDoS assault, the perpetrator sends TCP connection requests faster than the goal system can cope with. This can easily reason for community saturation.